Laptop monitoring. Computer spyware - what is it? How to install spyware on your phone
Applications and special programs on smartphones are increasingly used in our daily lives. We get used to using them to make purchases, conduct financial transactions, communicate with friends around the world. If you need to further monitor your child's social circle, listen to the conversations of company employees or family members, you will need a spy program for android or ios, which is easy to download and install on your smartphone. It will prove useful for monitoring children, the elderly, household staff or employees.
What is spyware
To use the phone monitoring service, you need to register on the website of the program developer. When registering, you need to remember your login, password to enter the service, confirm your phone number or email address. Spyware differs from each other in control functions, in the types of presentation to you of information "taken" from the controlled device. It can be a screen shot, call table, sms, call recordings. The program for spying on an Android phone must be downloaded, installed, and activated on a smartphone in secret from the user.
Types of spyware
Remote control programs for smartphones are divided into the following types:
Spy features
By controlling the smartphone, the Android spy program implements the functions of tracking and logging all the actions of the object. After collecting information, depending on the type of functions you have chosen, on your smartphone or computer via the Internet, the utility will provide the ability to receive data:
- a log of incoming, missed, outgoing calls of subscribers with their names, the duration of the conversation;
- audio recordings of telephone conversations;
- list and texts of all sms, mms messages with the time they were received or sent;
- photo and video information taken by the spy camera of the controlled device;
- the current location of the subscriber with online tracking of movements using geolocation using the base stations of the GSM operator or GPS navigation;
- browsing history of smartphone browser pages;
- accounting for downloaded, installed, used applications;
- sound control of the environment with remote control of the microphone.
Spyware for Android
Among the range of spyware offered, there are free utilities that, when analyzed and verified, turn out to be ineffective. To obtain high-quality information, it is necessary to spend funds for the collection and storage of photo, video, audio information. After registering on the developer's website, the client receives a personal account indicating the connected control functions and the information collected.
A paid program for wiretapping a mobile phone for Android is developed taking into account the need to satisfy the most fastidious customers in several ways:
- ease of installation;
- invisibility of being on a controlled smartphone;
- convenience for the customer to receive and save the collected information.
neospy
One of the simplest spyware for a computer or smartphone is Neospy. NeoSpy Mobile for the Android platform is a legal application that can be downloaded from Google Play. When downloading a new version of NeoSpy Mobile v1.9 PRO with installation, downloading the apk archive, settings are possible in which the program will not be displayed in the list of Google Play applications, it will be able to monitor the smartphone keyboard, intercept photos from the camera. The cost of using the program depends on the selected functions and will range from 20 to 50 rubles per day.

talk log
More serious is the Talklog Android phone spy. Before installing it on your smartphone, you will need to disable anti-virus software. You will need to allow installation of apps from other sources in your phone's security settings. The Talklog service is a full-fledged spy that can get almost all information about the activity of the monitored object. The utility has a free trial mode with its capabilities and several basic free functions. The cost will be from 10 to 50 rubles per day, depending on the functionality you need.

Flexispy
Spyware for Android Flexispy includes a huge number of ways to access your smartphone - intercepting SMS, MMS messages, wiretapping, recording telephone conversations, reading dialogues from 14 internal chats (Facebook, WhatsApp, Viber, Skype, WeChat, Telegram, etc.) , real-time call pickup, listening to the phone's surroundings through the microphone, more than 140 functions. The cost of using the utility is appropriate - the minimum Premium package will cost you 6,000 rubles for 3 months, the maximum Extreme - up to 12,000 rubles for 3 months of use.

Mobile Tool
MobileTool spy application for Android operating system will provide you with information about calls, SMS, MMS, phone location, phone book. It is able to remove its shortcut from the application list. Functions will be available to you - viewing photos, protection against theft by blocking the device, turning on the siren. All information will be available in your personal account on the application website. There is a two-day trial mode for checking the functionality, discounts depend on the period of use. The average payment for using the utility will be about 30 rubles per day.

Mobile Monitoring
Mobile spy for Android Mobile Monitoring (mobile monitoring) after registering on the site, choosing a tariff plan and paying, it will make it possible to save telephone conversations, the voice recorder function, save all SMS messages, geolocation of the phone's location, and build travel routes. The program works on smartphones of any mobile operators in Russia. The cost when choosing only geolocation will be 800 rubles for 3 months, full functionality - 1550 rubles for 3 months, with a 40% discount when paying for a year.

How to install spyware on your phone
Installation of a mobile spy begins with registration via the Internet on the manufacturer's website, choosing a tariff plan, and paying for services. Then a link is provided that must be entered in the smartphone browser to download the program. Some spyware for Android is available through Google Play, downloaded like regular apps. When installing and activating the program, you will need permission to access all the smartphone functions necessary for its operation. You may need permission to use programs that are obtained from unknown sources.
How to detect spyware on Android
Most spyware for Android has the function of masking its presence in the smartphone. They can exclude themselves from the list of applications, not show their activity during periods of using the phone. Many anti-virus programs can detect such software. To protect against spyware and malware, you should make a habit of running a full phone scan once a week or setting it to run automatically on a schedule. The main features of the work on the phone of such programs can be:
- slowdown of the mobile phone;
- rapid battery discharge;
- unjustified eating of Internet traffic.

Video
Personal Monitor
YOUR DECISION
for parental control
Need a keylogger?
2 500 000 . That is how many people (and this is more than the population of the whole of Latvia, for example) have chosen the Mipko Personal Monitor program as a keylogger. Why?
For at least 9 reasons:
Protection for your child
personal monitor for windows
Free version
for 3 days
Video review about Mipko Personal Monitor by Alexander Medvedev
Our proprietary guarantee for Mipko Personal Monitor
We guarantee that you will be 100% satisfied with Mipko Personal Monitor keylogger. After all, you can check all the features of the program in action for free - for this you have 3 days.
Well, if for some reason you are disappointed in Mipko Personal Monitor after switching to a paid version, then within 7 days after the purchase we will refund your money.

How Mipko Personal Monitor works
No matter how you want, but, for example, it is quite difficult to “block” a child’s access to dubious resources beyond their age. In addition, with a little digging on the Internet, inquisitive youth will find a way to get around any obstacles.
If you are worried about your children and want to know what sites they visit, where, with whom and what they are talking about, then Mipko Personal Monitor is the best solution. Why?
The program does not show itself in any way on the computer. The user is not even aware of its existence. At the same time, Mipko Personal Monitor collects a complete report on his actions and records everything that happens. What does it look like?
For example, as soon as your child logs in to VKontakte or logs out to Skype, Mipko Personal Monitor immediately captures all his actions. For example, it records voice calls, saves the history of correspondence, records pages viewed, and so on. You will receive the relevant reports to your e-mail.
In addition, all copies of the reports are stored on the computer's hard drive. However, a person who does not know about Mipko Personal Monitor will not find them. After all, the corresponding folder is hidden very deep, and the reports themselves are stored in encrypted form, and only Mipko Personal Monitor can read them.
“I have been using your program for almost a year - it has shown itself to be a very reliable tool with which I have never had any problems. We are also pleased with the performance of the program - it works almost imperceptibly.
Vitaly Makushev
Simplicity and elegance
Mipko Personal Monitor is a home keylogger. It does not have extra features that are in demand by corporate clients, but are absolutely meaningless on a home computer.
As a result, the program interface itself turned out to be very simple and understandable. Like the iPhone, which even a person far from technology will understand in 5 minutes. At the same time, the possibilities of Mipko Personal Monitor are as wide as possible and will more than satisfy even the most demanding user.
“I have been using your program for a long time. I like the interface and functionality of the program, and most importantly - its performance. I also see that you have not abandoned this project, updates and corrections are constantly being made. For which special thanks to you.
Mikhail Zinoviev
5 more arguments in favor of Mipko Personal Monitor

- - If Mipko Personal Monitor has a crash or a conflict with an antivirus, the program will still not impersonate or compromise you.
- - Mipko Personal Monitor has a completely Russian-language interface and technical support.
- - You are not left alone with the program, but receive any help and support from us even during the free testing period.
- - You decide how much hard disk space to allocate for storing Mipko Personal Monitor recordings, and this limit will never be exceeded.
- - You always know with whom and what your child or loved one is talking about, as well as to whom he makes appointments.
“Before I started using it, I tried many alternative keyloggers (I don’t remember the names anymore). Your program attracted me with its ease of use and visibility of the results.”
Sergey Minaev
Mipko Personal Monitor and antiviruses

Legally, Mipko Personal Monitor is not classified as spyware or malware by antivirus classification. In essence, this is an observer program that monitors what is happening on the computer and does not save any personal user data.
At the same time, only the administrator (owner) of the computer can install Mipko Personal Monitor by entering the appropriate password. This provides the program with legality and legitimacy from the point of view of the vast majority of antiviruses. As a result, they do not react in any way to Mipko Personal Monitor.
However, some anti-virus programs (not more than 5%) may interfere with the installation and operation of Mipko Personal Monitor. Then just let us know about it, and we will send you step-by-step instructions on how to make Mipko Personal Monitor and your antivirus friends.
“I am glad that the program is hidden, does not load the computer and works completely offline.”
Do you already have these questions?
How to deal with the safety of personal data?
Mipko Personal Monitor does not collect personal data and, moreover, does not send it to us. All information is stored on your computer and sent to you by email. At the same time, all letters go directly, bypassing our servers.
I'm with a computer on you, can I install Mipko Personal Monitor?
Yes, you can. The program interface is extremely simple. You literally need to press only two buttons and follow the detailed instructions. In addition, we are always ready to provide any assistance in this matter.
What should I do if I have problems with Mipko Personal Monitor?
Contact our support team and we will quickly resolve all issues.
“I have been a user of your program for quite some time now. I like the fact that the program has practically no analogues, helping out even in the most difficult cases. I have a son, and it is very important for my wife and I to know in what direction his interests are developing.
Spyware is used to control the work of computers of office workers and employees of enterprises. It is also a good solution for monitoring children while parents are not at home.
Computer spyware has nothing to do with malicious software. Mostly installed with the permission of the PC administrator and do not cause any harm. Viruses operate on a different principle, they are installed without the permission of the administrator, they deliberately spy on the user, collecting confidential information and transferring it to third parties. The management of companies and enterprises inform their employees about the established programs for controlling the production process.
Computer spyware
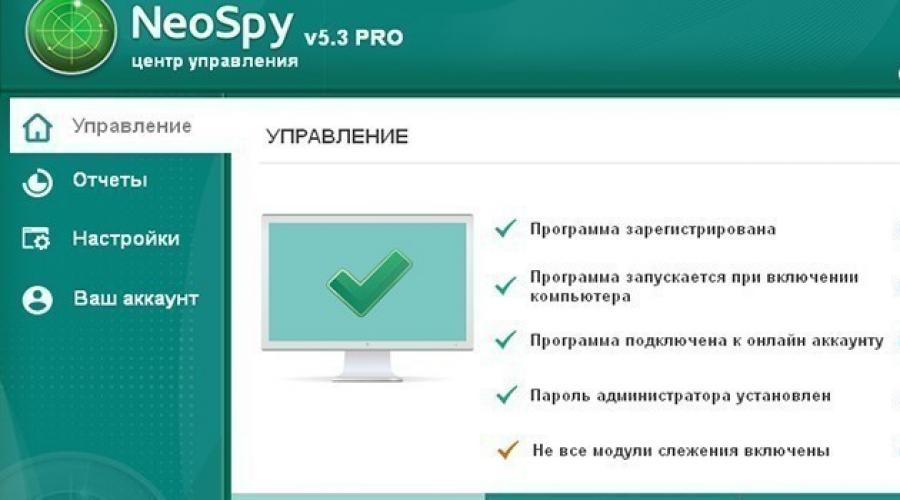
- this spy program is a universal tool for monitoring user actions on a personal computer. Several available installation options: administrator and hidden. With a hidden installation, processes are not displayed in the task manager. A program is used for home monitoring of children and control over the actions of employees at the enterprise. Neospy Software shareware, you can purchase a paid version at a price of 1990 rubles on the official website.
NeoSpy features:
- interception keyboard clicks;
- the possibility of creating screenshots;
- collection data about system events;
- tracking for using instant messengers and recording voice/video calls;
- report about the operation of the computer.
Advantages:
- Russian-language interface;
- functionality;
- real-time computer monitoring;
- hidden installation.
Disadvantages:
- universal English-language spyware. The main feature of this software is that it not only tracks user actions, but also blocks certain operations on the computer. When creating an account, users can add a ban on certain actions on the PC. To use the full functionality you need buy paid version at a price of $40.
Opportunities:
- monitoring typed text from the keyboard;
- report about system events;
- creation multiple accounts.
Advantages:
- creating a policy of prohibitions on performing certain actions on a PC;
- work in semi-hidden mode.
Disadvantages:

- used as keylogger, while having additional functionality:
- control over the contents of the clipboard;
- the ability to take screenshots of the screen;
- surveillance of visited sites.
The program has no special advantages, quite standard functions for such software are collected here. Of the shortcomings it can be noted that when using the module for tracking keystrokes on the keyboard, only English text is correctly recorded. 
Spy Go
This computer tracking software is for home use only. SpyGo can also be used to track employees of offices and enterprises. Program shareware, you can purchase the full version at a price of 990 to 2990 rubles, depending on the set of options.
Opportunities:
- keyboard spy;
- record system events on the PC (launching applications, working with files, etc.);
- the control visits to web resources;
- receiving images from the user's screen in real time;
- obtaining information about the contents of the clipboard;
- opportunity to receive microphone recording(if connected).
Advantages:
- work in covert surveillance mode;
- computer reports;
- tracking search queries and time spent visiting Internet sites.
Disadvantages:

snitch
Snitch is an easy-to-use spyware that allows you to monitor user activities on a PC.
Opportunities:
- monitoring keyboard, clipboard and system events;
- tracking user actions on the Internet and in instant messengers;
- drafting summary reports about the operation of the computer.
Advantages:
- blocking the forced termination of the process in the task manager;
Disadvantages:
- there is no hidden mode of operation;
- antivirus conflicts.
- the utility is a keylogger that allows you to save data entered in the windows of any programs, browsers, instant messengers, etc. Also provides detailed report in PC operation. The program runs in stealth mode, does not appear in the task manager, and does not create shortcuts on the desktop or start menu. The program can buy at a price 49$.
Opportunities:
- reading typed texts from all filling forms;
- hidden mode of operation;
- receiving screen data user in real time;
- sound microphone recording.
Advantages:
- functionality;
- provision of summary reports;
- hidden mode of operation.
Disadvantages:

Expert Home
Expert Home is a free computer activity tracking software that allows you to track and record all user actions. This software is mainly used to provide parental control.
Opportunities:
- interception keyboard clicks;
- creation pictures screen;
- blocking certain actions on the computer;
- providing reports about system events on the PC.
Advantages:
- hidden mode of operation;
- convenient navigation;
- undemanding to resources.
Disadvantages:

SC-KeyLog
Free keyboard tracking software. Additionally, SC-KeyLog has the ability to collect data on mouse clicks.
Opportunities:
- data collection entered from the keyboard;
- tracking visited sites;
- stealth mode work;
- report with information about actions performed from the PC.
Advantages:
- distributed free of charge;
- collection of data on all actions on the PC (launching applications, working with files).
Disadvantages:

- fully free keylogger for Windows 7/8/10 that allows detailed monitoring of user activity. Ideally used as a means of parental control.
Opportunities:
- invisibility in the task manager;
- collection entered data from the keyboard;
- tracking visited websites.
Advantages:
- free distribution;
- functionality;
- user-friendly interface.
No flaws were found in the program. 
winspy
- this spyware is used as a means of parental control and monitoring the activity of employees on computers.
Opportunities:
- remote installation;
- interception text information from the keyboard;
- hidden operating mode.
Advantages:
- undemanding to the resources of the operating system;
- functionality.
Disadvantages:

Vkurse for Android
Vkurse - device spyware running Android OS. Allows real-time tracking of user actions on a phone or tablet.
Opportunities:
- simultaneous control for all instant messengers running on the device;
- allows to take a photo screen;
- tracking entered text information from the Android keyboard;
- detection using GPS;
- record incoming and outgoing calls.
Advantages:
- hidden mode of operation without an active window;
- the ability to install without root;
- does not boot the system.
Disadvantages:
- the ability to detect applications through the "Task Manager" (task manager).
How to detect spyware on your computer
If the spyware works in stealth mode, it is quite difficult to detect it. Our review used only legal software, which is not malicious, but at the same time it can be detected by antiviruses. It is recommended to add such software to exceptions. If you do not need to uninstall the program, but only need to mask your actions on your PC from it, use anti-spyware tools that will block the interception of keystrokes.
Instruction
The need to control actions user can be caused by a variety of reasons. For example, you want to keep track of your subordinates or check what your child is doing while working on a PC. Most often, the addresses of visited websites, launched during the operation of the program, and information entered from the keyboard are of interest.
Tracking visited Internet resources is very simple, for this it is enough to view the history (log) folder in the browser. You will see all the sites that the user visited. True, experienced users, having worked on, can clear the visit log or remove individual entries from it.
The most reliable way to control user is the installation of a tracking program on the computer. For example, you can use the free KGB Key Logger program. It will allow you to be aware of everything that the user does on the computer. It has a visible and invisible mode, monitors keystrokes, keeps track of visited sites, can take screenshots (screenshots). The intercepted information can be sent to the mailbox. At the same time, the program is absolutely legal, as it is installed on the computer by its owner.
Similar functions are provided by the ExtraSpy Employee Monitor program, which was created to provide management of enterprises with control over their employees. By installing this program on a computer, you will always be aware of what the person working on it is doing.
To remotely administer a computer, you can use the Radmin program. By installing its server part on the computer on which you want to control the work, you can connect to it via the Internet at any time. You will see the screen of the remote computer updated in the current time mode in the program window, you will see all actions user. In addition, you can view any folders and files, copy and delete information, run and close programs. This program is legal, you can download it from the manufacturer's website: http://www.radmin.ru/.
Related article
The person exercising control always comes under psychological pressure from the people controlled by him. Both parties perceive the quality level of the work performed work in my own way. To avoid conflicts and unnecessary emotional experiences, it is necessary to establish quality control rules that are unambiguously perceived by all participants in the process.

Instruction
Define goals. Describe specifically, quality" and what are the criteria for determining it. Vague and vague wording will not allow effective control of the process. If the quality consists of many parts, make a list of them. Describe in detail the quality criteria for each item.
Set to determine the quality level. Use the criteria described earlier for this. Rules should be written in the form of step-by-step instructions. It will help to argue your conclusions on quality control in case of conflict situations. To convince the interlocutor, it will be enough to tell you step by step how you exercised control.
Set breakpoints. These are the gaps work in which quality control is carried out. People shouldn't flinch at your sudden appearance. Explain clearly at what stages work and why control is needed.
Related videos
note
Stop any attempt to reduce quality. Don't do favors. Otherwise, the rules will be deliberately ignored.
Helpful advice
Count the quality work. What is considered, people subconsciously strive for. Publicly encourage leaders with kind words. People don't want to spoil their performance.
If a child spends most of his free time on the computer, parents may be interested in what websites he visits, what games he plays and what movies he watches. Sometimes vigilant spouses, in the name of preserving the family and peace of mind, are also not averse to checking what their dear half is doing on the Internet.

Instruction
You can purchase a hardware keylogger - a device that tracks keystrokes on the keyboard. Depending on the model, it connects to a USB connector or is inserted into the keyboard. Reports can be written to a special folder or sent over the Internet to another computer. The price of the device depends on the range of its functions and the amount of memory.
You can use a keylogger software such as Elite Keylogger. The developers claim that the program runs at the kernel level of the operating system and is therefore completely invisible to anti-spyware. Run the program and select one of the operating modes Visible mode ("Visible") or Unvisible ("Invisible"). For preliminary acquaintance and training, it is better to use Visible mode.
On the Logs menu, click View logs and enter the password you will use to view the logs. Mark the date you are interested in on the calendar and click View logs for… The left side of the window will display the user account, the list of keys pressed, the date and time of the event.
program every three minutes. To view screen thumbnails, select the Screenshots menu item. You can call the full-screen view mode by double-clicking on the thumbnail. The Internet Activity section contains a list of visited websites.
Similar functions are performed by the keyboard Eltima Powered Keylogge. This program also monitors keystrokes, takes screenshots at regular intervals and can send logs to a given e-mail. The program is invisible to anti-spyware and is password protected
These programs are shareware. You can use the Punto Switcher utility, which is fully distributed by the developer. Few people suspect about its spy capabilities, because its main purpose is to switch the keyboard layout and frequently used words with a certain key combination.
Install the program on your computer and right-click on its icon. In the drop-down menu, select the "Settings" section and in the left part of the settings window, check the "Diary" item. Check the boxes "Keep a diary", "Automatically save the contents of the buffer ...", "Keep a diary in exception programs".
Click the "Set password ..." button and enter a combination of numbers and symbols. Use the Apply and OK buttons to confirm. To view entries in the context menu, select "Settings", then "Open diary".
Related videos
note
It will not be possible to hide the spy functions of Punto Switcher - everyone who guesses to check its settings in the drop-down menu will find out about them. However, only those who know the password can read the contents of the diary.
Proper management of a business enterprise involves control over all its components. If you lose sight of this control lever, the system quickly falls apart, left to itself. Competent control begins with planning, setting tasks and assigning responsibilities.

Instruction
Identify the tasks that need the most management oversight. In any company there are main divisions that perform the main production functions, as well as auxiliary departments, whose activities are not decisive and do not directly affect the final result. By compiling a hierarchy of functions, you can prioritize areas that require special attention.
For each structural unit or stage of work, if we are talking about an unfolding business project, appoint people who will carry out leadership. Clearly define the range of functional responsibilities of middle managers and the limits of their powers. To control his area of work, each manager must have a real opportunity to influence the state of affairs and intervene in the production process.
Develop and implement a system of standardized reports from the heads of structural divisions. You must systematically obtain information that characterizes the performance of the company in all areas. This is one of the important conditions when setting up a control system. The data is brought together, systematized and correlated with the planned indicators.
Put into practice visits by the management of the enterprise to individual production sites. This will allow to assess on the spot how efficiently the work is going, and will also create appropriate motivation among the staff. Knowing about the possibility of unannounced inspections, employees will be more responsible in the performance of their duties. Visiting grassroots departments also provides an opportunity to get the feedback needed to make management decisions.

At this time, it is time for the leader to think about the need to change something. There is no need to make hasty decisions about downsizing, installing video cameras in the office. It is enough just to purchase a special software package. Control of staff computers will allow you to gently "stimulate" subordinates and direct their work in the right direction.
There are a number of programs that allow you to discreetly track what an employee is doing at the workplace. All of them offer a fairly wide range of functions:
Tracking queries in search engines. The function will help determine what employees are looking for more often during working hours: new customers, or popular videos.
Taking screenshots periodically.
Checking the start and end times of work on the computer, time intervals of user inactivity, simple.
Control of employees' computers here for the work of the mouse and their keyboards (it will allow you to track which keys were pressed and how often).
Printer tracking (document names, printed text volume, etc.)
Control over the operation of removable media (which files were copied from a computer to a USB drive and vice versa).
Control of correspondence in skype and icq.
When using the program, the manager receives a daily report on the work and inactivity of each user at his computer, as well as diagrams of working hours.
Most spyware vendors offer 15-30 business days of free testing of their product. Usually this time is enough to determine whether there is a need to purchase such a software package at the enterprise. The control of computers of working personnel is a fairly budgetary process. The cost of a license for one computer, depending on the functions performed, starts from 450 rubles, but the expenditure of these funds is justified. Losses of working time are reduced by 20-40%. And the employees themselves, who are aware of the established program control, stop doing personal business from 9-00 to 18-00.
It is logical that such self-organization of employees is in the interests of management. Someone prefers not to inform about the installation of such programs, while others, on the contrary, carry out the implementation indicatively. The main thing is that in the end there should be a result, and the effectiveness of personnel indicators will increase exponentially.
How can you find out what your child or employee is doing on the computer? What sites does he visit, with whom does he communicate, what and to whom does he write?
To do this, there are spyware - a special kind of software that collects information about all its actions unnoticed by the user. A spy program for a computer will solve this problem.

Spyware for a computer should not be confused with a Trojan: the first is absolutely legitimate and is installed with the knowledge of the administrator, the second gets on the PC illegally and carries out hidden malicious activities.
Although malicious programs can also be used by legitimate tracking programs.
Spy applications are most often installed by business leaders and system administrators to control employees, parents to spy on children, jealous spouses, etc. At the same time, the “victim” may know that she is being monitored, but most often she does not.
Overview and comparison of five popular spyware
NeoSpy
NeoSpy is a universal keyboard, screen and user actions spyware. NeoSpy works invisibly and can hide its presence during installation.
The user who installs the program has the opportunity to choose one of two installation modes - administrator and hidden. In the first mode, the program is installed openly - it creates a shortcut on the desktop and a folder in the Program Files directory, in the second it is hidden.
Program processes do not appear in Windows Task Manager and third-party task managers.
The functionality of NeoSpy is quite wide and the program can be used both as home tracking and in offices to control employees.
The spy program is distributed in three versions under a shareware license. The price is 820-1990 rubles, but it can also work for free (even in hidden mode) with restrictions when viewing reports.
What can NeoSpy do:
- monitor the keyboard;
- monitor site visits;
- show the user's screen in real time via the Internet from another computer or from a tablet;
- take screenshots of the screen and save pictures from the webcam;
- control system events (turning on, turning off, downtime in the computer, connecting removable media);
- intercept the contents of the clipboard;
- Monitor the use of Internet messengers, record Skype calls;
- intercept data sent for printing and copied to external media;
- keep statistics of work at the computer;
- send laptop coordinates (calculated over Wi-Fi).
Thanks to the Russian-language interface, a wide range of functions, correct keyboard interception and a mode of operation completely hidden in the system, NeoSpy gets the maximum rating when choosing user control software.
Real Spy Monitor
The next spy is Real Spy Monitor. This English-language program not only has tracking functions, but can also block certain actions on the computer. Therefore, it is often used as a means of parental control.
For each account in the settings of Real Spy Monitor, you can create your own policy of prohibitions, for example, to visit certain sites.
Unfortunately, due to the lack of an English-language interface, it is more difficult to figure out how Real Spy Monitor works, despite the graphic thumbnails for the buttons.
The program is also paid. The license costs from $39.95.
Features of Real Spy Monitor:
- interception of keystrokes, clipboard contents, system events, websites, instant messengers, mail;
- work in semi-hidden mode (without an active window, but with the display of the process in the task manager);
- work with multiple accounts;
- selective autostart for different accounts.
In general, many users like Real Spy Monitor, among the shortcomings they note the high cost, the lack of a Russian-language interface and the display of the process in the task manager.
Actual Spy
Developers position Actual Spy as a keylogger (keylogger), although the program can do more than just record keystrokes.
It controls the contents of the clipboard, takes screenshots, monitors website visits, and other things that are included in the main set of spies we have reviewed.
When installed, Actual Spy creates a shortcut in the Start menu, so it can be seen by the user. The launch also occurs openly - to hide the program window, you must press certain keys.
Opportunities Actual Spy is not much different from the capabilities of competitors. Among the shortcomings, users noted that it correctly records keystrokes only in the English layout.
Spy Go
SpyGo is a spy kit for home use. It can also be used in offices to control employees.
To start monitoring, just click the "Start" button in SpyGo.
SpyGo is distributed under a shareware license and costs 990-2990 rubles, depending on the set of functions.
In trial versions, the duration of monitoring is limited to 20 minutes per day, and sending reports to e-mail and via FTP is not available.
Main features of SpyGo:
- keystroke monitoring;
- recording of all actions on the computer (launching programs, operations with files, etc.);
- control of visits to web resources (history, search queries, frequently visited sites, duration of stay on the site);
- recording what is happening on the screen;
- saving the contents of the clipboard;
- listening to the environment (if you have a microphone);
- monitoring of system events (time to turn on and off the computer, downtime, connecting flash drives, disks, etc.).
Important! The disadvantages of SpyGo, according to users, include the fact that it does not support all versions of Windows, often throws errors when sending reports, and is quite easily unmasked.
snitch
Snitch - the name of this program is translated as "snitch", and it is very unfriendly towards the user. Snitch spies on computer activity. It works hidden, does not require complex settings and has little effect on system performance.
The program is released in a single version.
Snitch Features and Features:
- monitoring of the keyboard, clipboard, system events, web surfing and communication in instant messengers;
- compilation of summary reports and schedules of controlled events;
- undemanding to the network configuration;
- protection against unauthorized termination of the program process;
- monitoring is carried out even in the absence of access to the network.
Of the shortcomings, you can notice conflicts with antiviruses
How to detect a spy on a computer?
Finding spyware on a computer that does not show itself in any way is difficult, but possible.
So, despite the legitimacy, the applications we have considered can recognize special antiviruses,"sharpened" for the search for spyware (trojans with espionage function), so we recommend adding the installed program to the exclusion list of such antiviruses.
And if you don't need to remove the spy, but only need to disguise your actions from it, you can use anti-spyware tools that, despite actively spying on you, will prevent interception of keyboard events and screenshots.
Then your correspondence and passwords will not fall into the wrong hands.