kali linux tools. Kali Linux - the main features of the system. Download Links for Kali Linux
Read also
Download Kali Linux. How and where?
Hello everyone, this is Computer76 and now I will present you an article on how to download Kali Linux correctly. Why do this, the question for you, I think, has already been resolved, and therefore immediately to the point.
Where to download Kali Linux?
The question of where to find Kali Linux, as such, is not worth it. Since the system is free to distribute and copy, there are more than enough sources. I will offer a few of them, but I will focus on some options that are most convenient for the user. I include among them those cases when you download Kali Linux in the form of an operating system image ready for burning to disk.
The first source to download Kali Linux is, of course, offsite.
Here on the English site all the latest versions of stable and Russian systems are available. The official website is located at:
Actually, this is the download page, where you can choose to download the disk image directly from the site or through the tracker also from the official site.
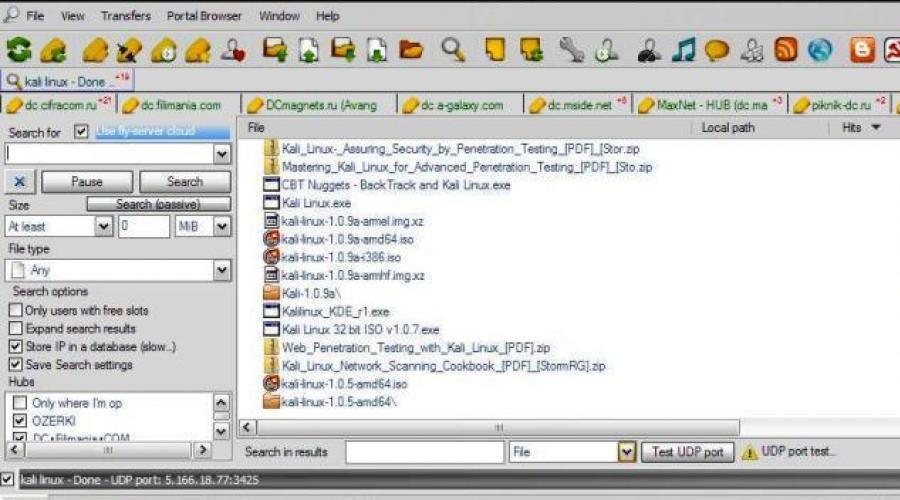
The second option is how to get the system in your hands (for those who know how to use peer-to-peer networks - this is the easiest way) - a local network, as it is popularly called. How to use a peer-to-peer network, configure it correctly and search for information correctly, read in this article. To explain this option, I will give only the search results that I got when I requested to search for the image of Kali Linux. The client program is connected to the maximum number of hubs, and therefore the results were not long in coming. Here's what happened to me:

Download - I don't want to.
The third option that cannot be discounted is torrent trackers. Fears about a deep and thorough cleansing of trackers are being realized, and therefore there are fewer and fewer files available for download. But, given the fact that Kali Linux is an open source operating system, it will be free for download for a long time. I will give an example of a page of my favorite torrent tracker with search results for the desired operating system.
 And here is another good site in terms of getting to know the programs. Similar to above:
And here is another good site in terms of getting to know the programs. Similar to above:
http://torrent-soft.net/
Access problems? freegate- proxy application for all browsers.
All you have to do is go through the simple registration procedure and start downloading the torrent. It takes crumbs, within a few kilobytes. When you launch a torrent file, the torrent client will come into play, pre-installed on your computer or the executable file of its portable version (whichever is more convenient for you). As a torrent client, I can personally suggest BitTorrent. I always use it.
Probably all sorts of ways to download Kali Linux are right in front of your eyes. Let's start burning to a disk or installing from a USB flash drive. Who forgot how, please search the site. There I described one of the recording options. I also offer to your attention the option of installing Kali on a USB flash drive, followed by launching from it and the ability, which is extremely important, to update and save all changes: .
Security issues of operating systems of built organizational networks have always been the most important aspect of administration. A lot of work had to be done to diagnose the presence of vulnerabilities, and often even after that there were loopholes for attackers. Such manipulations have been noticeably simplified with the advent of Kali Linux. Instructions for its use are mostly available only in English. Such a system is not suitable for permanent home use, especially since it is not recommended for beginners. This is a professional tool that needs to be learned to use and requires fine tuning. And this requires sufficient experience and a complete understanding of the actions performed.
Important Warnings
The capabilities of the Kali Linux operating system are so wide that not everyone uses them to improve the security of their own system. Often it becomes a convenient tool for illegal actions of intruders. Therefore, it is important to understand already at the initial stage of acquaintance that certain manipulations that the system allows you to perform may be illegal. Even installing and learning about Kali Linux for educational purposes can backfire in some countries.
As a small piece of advice, we can give a recommendation to install the system on and work through VPN, if you do not want to be limited to its superficial study. When starting, it is also necessary to use keys that will avoid problems with the law.
What is Kali Linux
The predecessor of Kali is BackTrack Linux, which is quite famous in narrow circles. The second one is based on Debian, and it provides support for packages and applications developed for this OS, which allows you to make your work quite comfortable through the use of familiar tools. If necessary, it will be quite easy to find programs for Kali Linux as well.
The distribution includes all sorts of utilities that allow you to conduct a full security audit to prevent intrusions. Running services, access to a computer through a network, web applications used, and much more can be analyzed using the tools available in Kali Linux.
As you can already understand from the name, the system is based on the Linux Kernel. The first version of the distribution was released more than two years ago. It contained all the most basic, the main emphasis was on functionality, and not on external attractiveness. But the great popularity of the system, its active use in a professional environment led to the need to make changes to the distribution.
User reviews of Kali are mostly positive. The system has become more stable compared to BackTrack, the set of programs and utilities has expanded, but on some laptops, sometimes the operating system stops seeing the built-in Wi-Fi adapter. This happens while using Live-launch from a USB flash drive, the problem is fixed by using an external adapter or installing the OS on a hard drive.
Changes in the new version

At the end of last summer, Kali Linux 2 was released. Thanks to the update, the system has become much more stable and the working interface is more attractive. In addition, many utilities have become obsolete for such a long period by the standards of information technology. If earlier you had to search for and install new versions yourself, now this work is done by the system itself, which allows you to keep them up to date without much effort. In addition, the system itself received support for rolling distribution mode.
Technical features

The basis of the new distribution is Linux Kernel version 4.0, included in the Debian Jessie release. Gnome 3.14 is currently used as the workspace, and the workspace has acquired an updated style and interface, the menu has changed somewhat in individual items.
Available assemblies
At the moment, there are various distributions that are convenient to use under certain conditions. You can easily find Live builds, images for popular virtual machines, installation packages. In addition, instructions are provided, following which you can prepare the assemblies yourself. If necessary, you can build your own image to work with ARM, work with this architecture is perfectly supported, providing a multiplatform system. Then it will become possible, for example, to install Kali Linux on a tablet or smartphone.
For those who already had the first version installed, it is possible to upgrade to the second one within the system. It is enough to use a set of commands, including obtaining a new distribution kit and installing it. Details can be found in the official accompanying documents.
Getting started with the system. Theoretical basis
The extensive capabilities of the system are difficult to know without studying the Kali Linux documentation. Instructions for use, unfortunately, in the form of detailed manuals for fine-tuning, are available on the official website, mainly in English, as in most other sources. However, a large number of fans gave birth in the established community to the emergence of detailed Russian-language manuals based on their own practice. In addition, there are training courses in Russian for both entry-level and more advanced specialists for professional corporate work.
Practical development

To study the system, it is enough to install it in any available and most comfortable way, especially since a large selection of available Kali Linux 2 distributions allows this. However, it is for educational purposes, especially at the initial stages, that it is better to use a virtual machine. This will be enough to study the set of utilities that are included, get used to begin to confidently navigate the system.
When learning how to work with Kali Linux, instructions for use are a must. In addition to the fact that the OS has rich features that are difficult to learn without any documentation, installation will require configuration that will allow them to be used most effectively.
The practical development of tools is best done on your own equipment in order to prevent possible problems with the law if the actions taken are contrary to it, and somehow the fact of their implementation becomes known to third parties.
Run from a flash drive

After completing the learning phase, you will want to use the system to analyze security and eliminate the identified weaknesses in existing networks in a company or at home. The easiest way is to always have a ready-to-run distribution kit with you if necessary. This is quite easy to do if you use specialized programs for a working operating system, for example, Rufus. It can often be useful to have support for saving files on a system installed on a USB stick and after rebooting it. Such an opportunity is also provided, but it is important to remember that for the described persistence mode, at the beginning of each boot, you will need to specify the appropriate mode so that the normal live mode does not start. In addition, if in a simple version a 2GB flash drive is enough, then in the latter case, additional space will be required to create a separate partition in which the necessary data will be stored.
Why is it useful to use Kali Linux?

Attackers in their work use specialized tools that can significantly reduce the time required for unauthorized penetration into the network. For example, with the help of Kali Linux, hacking becomes much easier and more convenient, especially when passwords and hardware settings that are set by default are not changed. Unfortunately, even in large corporations, this happens quite often. After that, obtaining the necessary data is a matter of technology; for a qualified specialist, the whole process is not particularly difficult. It is all the more important to use the same tools to identify vulnerabilities in your defenses in order to make it harder for such people. A simple practical example is the hacking of Wi-FI routers, which are currently installed in almost every apartment, not to mention organizations.
Penetrating the network through Wi-Fi
To hack a Wi-Fi router, it is enough to organize a password search. But even on high-speed hardware, this takes a lot of time. Modern routers use the WPS protocol, which is designed to simplify network setup. Not all users understand the security of wireless networks, they need all possible help in setting them up. With the use of this protocol, there is no need to set the WPA / WEP encryption parameters, which provide protection against unwanted access, manually, they, like the network name, are set automatically by pressing a button on the router. It would seem a great idea, but, as often happens, vulnerabilities were found here, using which a password can be cracked in a few hours.
Not only does the WPS pin code consist of 8 characters, the last of which is enough to check it in blocks, and not in its entirety, as a result of which the number of possible combinations is reduced to 10998. Using Kali Linux, it is quite easy to hack a Wi-Fi network through the included WPS and it won't take long. A utility that will monitor the network is enough, and one that directly enumerates the pin code. For greater clarity, you can check how easily and quickly this happens on a home router.
Thus, to protect yourself, it is better to disable WPS on the router, where this option is active by default. Otherwise, every neighbor, even a student, will be able to connect to the network and use it. The instructions for use are quite simple, this is one of the most common examples on all resources dedicated to this operating system.
kali linux wifi hack

In short, using the iwconfig command, we determine the available network interface (as a rule, it is called wlan0, but it may differ).
After that, we start monitoring the active interface:
airmon-ngstartwlan0
To find out which networks are in scope, run the following command:
Where mon0 is the name of the previously running monitor.
From the entire list that appears, only those networks that have WPS enabled are of interest. The command is used to define them.
Now you can choose any target you like and start selecting a pin code:
Reaver -I mon0 -b -a -vv
The BSSID from the result of the previous command is written here. If everything is done correctly, then the password search will start. On average, the network is hacked from four to six hours. But some new router models have protection against WPS attacks and turn off brute force after a certain number of unsuccessful attempts.
And this is just one side of Kali Linux. Instructions for use will give a comprehensive understanding of the capabilities of the system.
Kali Linux is designed to test systems for vulnerabilities, conduct audits, analyze residual information, and identify the consequences of intruder attacks. It contains many utilities for conducting penetration testing: from analyzing the vulnerabilities of web applications to hacking networks and services and fixing them in the system.
Kali includes one of the most comprehensive collections of tools for computer security professionals, from web application testing and wireless penetration testing to RFID reader.
Kali Linux comes with a collection of exploits and over 300 specialized security tools such as Aircrack, Maltego, SAINT, Kismet, Bluebugger, Btcrack, Btscanner, Nmap, p0f. In addition, the distribution kit includes tools for accelerating password guessing (Multihash CUDA Brute Forcer) and WPA keys (Pyrit) through the use of CUDA and AMD Stream technologies, which allow using GPUs from NVIDIA and AMD video cards to perform computational operations. In addition, the distribution includes the metasploit-framework package, which contains the Metasploit components and the exploit database. All the dependencies needed to run Metasploit are bundled into one package, making it easy to install Metasploit Community / Pro from the Rapid7 website.
All original developments created within the distribution are distributed under the GPL license and are available through a public Git repository. A full iso-image, 2.8 GB in size, and a truncated image based on the Xfce desktop, 1 GB in size, have been prepared for download. Builds are available for x86, x86_64, ARM architectures (armhf and armel, Raspberry Pi, ARM Chromebook, Odroid).
The key change in the new release is the use of a rolling update delivery model, in which software versions in the distribution are always kept up to date, and new releases are delivered as they become available, without the need to periodically upgrade to new distribution releases. System updates are imported from the Debian testing branch, updates to versions of security testing tools are released by the Kali Linux developers within a few days of the release of the new version. To track new releases of security testing tools, a special web-based Kali Linux Package Tracker has been prepared.
Features of the new release:
Like the previous version, the new distribution is multi-platform and supports the following ecosystems: x32, x64
The update touched, first of all, the stability of the work.
The distribution is based on the Linux Debian kernel, the number of drivers for hardware support and wireless Wi-Fi adapters has been significantly increased. The user is offered a choice of desktops based on LXDE, Xfce, MATE, e17 (window manager (WM) for the X11 system in Linux).
Updates: support for rolling distribution mode (rolling release).
Relevance: monitoring and updating utilities included in the distribution.
Workspace: new style, menu composition and user interface.
Checking Utilities Versions
- The distribution system is integrated into the system of checking versions of the main utilities. They will also be updated promptly as new versions are released.
New design
Support for ARM and NetHunter
- Kali Linux 2016.2 officially runs on Raspberry Pi, Chromebooks, Odroid, etc. Kernel sources are posted in the ARM images section to make it easier to compile new drivers.
The developers of the famous pentesting distribution have made the most significant release since 2013. Kali Linux 2.0 has been officially announced. The distribution is based on the Linux 4.0 kernel, the number of drivers for hardware support and Wi-Fi has been significantly increased, support for various desktop environments (KDE, GNOME3, Xfce, MATE, e17, lxde and i3wm) has been implemented, the list of utilities in the kit has been updated. But most importantly, Kali Linux is now distributed in a rolling distribution mode.
Continuous update mode
Kali 2.0 will be continuously updated through the Debian Testing infrastructure as new stable packages are released.
Checking Utilities Versions
The distribution has an integrated system for checking versions of the main utilities. They will also be updated promptly as new versions are released.
New design
Implemented native support for KDE, GNOME3, Xfce, MATE, e17, lxde and i3wm desktop environments. By default, the system switched to GNOME 3, after a long period of refraining from such excesses. If desired, users can activate multi-level menus, a transparent console, and many other "chips" of GNOME 3. True, because of this, the requirements for RAM have increased: in the full version, "gnome" needs 768 MB of RAM. For low-power computers, a minimal build of Kali 2.0 ISO has been released, where the memory consumption is much less and the lightweight Xfce environment is used.
Support for ARM and NetHunter 2.0
Kali Linux 2.0 officially runs on Raspberry Pi, Chromebooks, Odroid, etc. Kernel sources are posted in the ARM images section to make it easier to compile new drivers.
The NetHunter mobile penetration testing platform has also been updated and runs on Kali Linux 2.0. Several new images have been posted, including for Nexus 5, 6, 7, 9 and 10.
Updated images for VMware and VirtualBox
If you are running Kali Linux in a virtual machine, then you can get fresh images from this link. There are 32- and 64-bit versions with a full-fledged GNOME 3 environment.
Upgrading to Kali Linux 2.0
There are two options: download the latest version and install the system from scratch, or run the upgrade procedure from 1.0 to 2.0. In the second case, edit source.list and run the following procedure.
Cat /etc/apt/sources.list deb http://http.kali.org/kali sana main non-free contrib deb http://security.kali.org/kali-security/ sana/updates main contrib non-free EOF apt-get update apt-get dist-upgrade # get a coffee, or 10. reboot
Metasploit
Unfortunately, at the request of Rapid7, the Metasploit Community / Pro package was removed from Kali Linux, leaving only the base metasploit-framework framework. The Metasploit Community / Pro version will have to be manually downloaded from the Rapid7 website after registration and obtaining a license.